Crypto wallets play a key role in the interaction with the cryptocurrency world, services, applications, and trading terminals. There are various types of crypto wallets in the industry: hot and cold, software and hardware, cloud and installable. Today we will talk about free hot software wallets, namely, web extensions, desktop applications, and web applications. This article describes their features, differences, pros, and cons.
Desktop Wallets
A desktop crypto wallet, as its name implies, is a crypto wallet that is downloaded, installed, and executed directly on your computer or laptop. Such wallets are generally considered safer than web versions since private keys and other required files are stored directly on the user’s device.
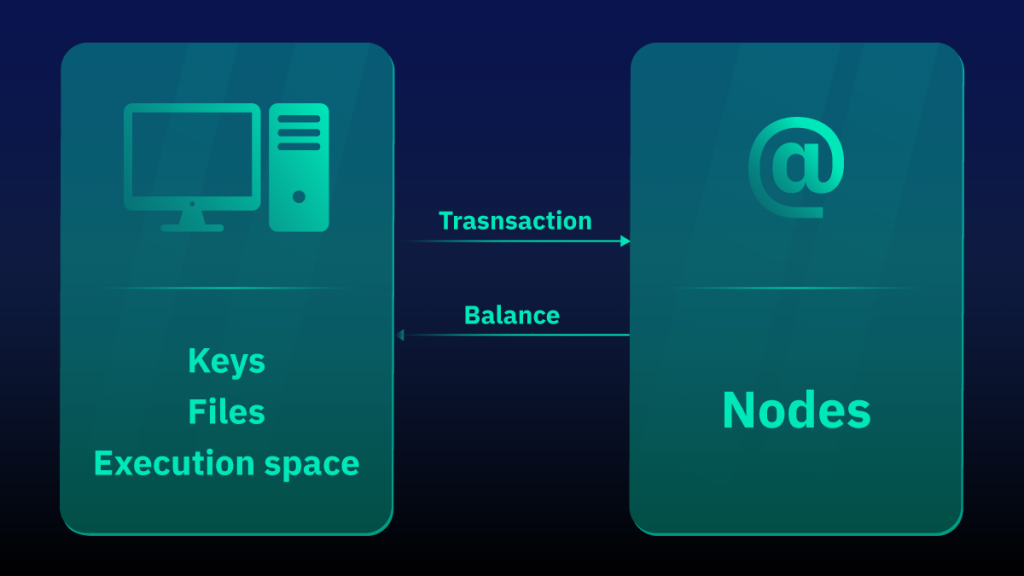
This type of wallet is classified as a hot wallet since it requires an internet connection (network nodes) to complete transactions. You should therefore be careful and ensure that your computer is well protected from all kinds of software threats such as software infections and malware.
In addition, we recommend that you keep a copy of the keys on the reserve device so that in the case of damage or loss, you can restore access to the wallet and secure your assets.
+ Keys and assets are yours alone;
+ Allows you to generate TX offline and send it to the network when a device is connected to the internet;
+ Advanced functionality and hardware wallet support;
– Vulnerable to infections and malware on your device;
– The loss of a seed phrase or a private key threatens a complete loss of assets.
Examples: Exodus.io, Jaxx.io, Electrum.
Web Applications
Web wallets are cryptocurrency wallets that run on the developer’s servers and are accessed by users through a web browser. The advantage of such wallets is that they can be accessed from any device with a browser and internet connection. All operations are performed on the cloud without requiring any download or installation — a user simply interacts with the website’s interface.
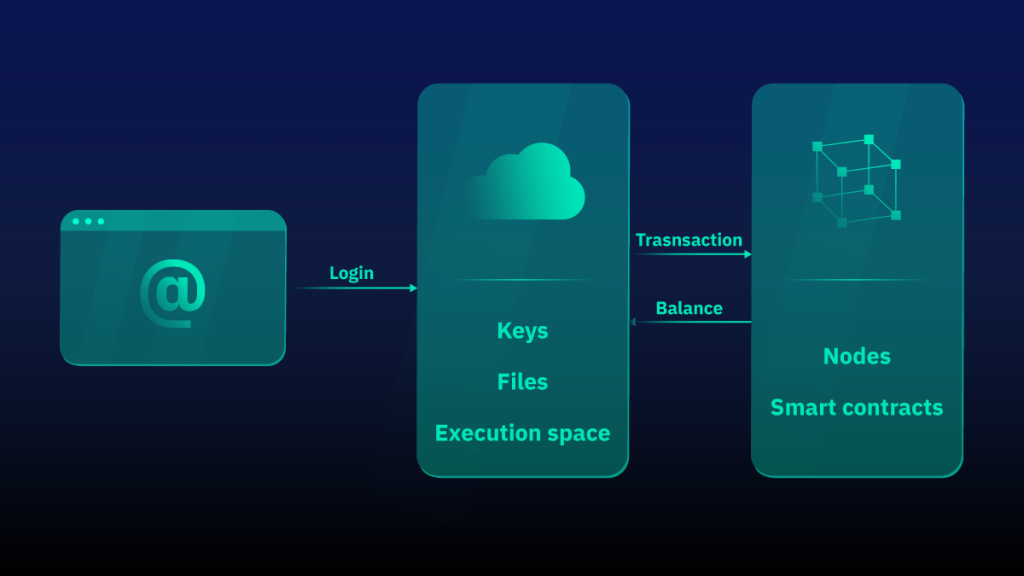
Often, access to such a wallet is simply granted through a username and password pre-set by the user. Thus, keys and assets can be stored on the developer’s side. This is the easiest, but at the same time, the least secure way to store and work with crypto assets. Even large custodial crypto exchanges that operate on the same principle (+ trading terminals) have been hacked.
+ Access from any device with an internet connection and a browser;
+ Many web wallets provide the ability to restore access via email or KYC verification;
+ Don’t require memory on the device as all info is stored in the cloud;
+ Some of these wallets can be used to interact with dApps;
– Mostly custodial, and keys are often available to developers;
– Must always be connected to the internet;
– Registration may be required;
– Lots of low quality or outright scam wallets.
Examples: MyEtherWallet, Polkadot.js, Binance exchange
Web Extensions
A crypto wallet extension is a browser-based wallet that works like a classic web extension (such as VPN, AdBlock, Grammarly, etc.). Extension wallets owe their popularity to the rise of decentralized finance and the numerous protocols that require special permissions to interact with addresses. When using an extension wallet, most protocols simply send a ready-made transaction with a request for the necessary permissions to the user’s wallet, which then only needs to be signed.
Unfortunately, some protocols can often be a scam concocted by unfriendly developers. You should only connect to protocols that you trust. Advanced users can also check the transaction details to ensure the interaction is secure before signing it.
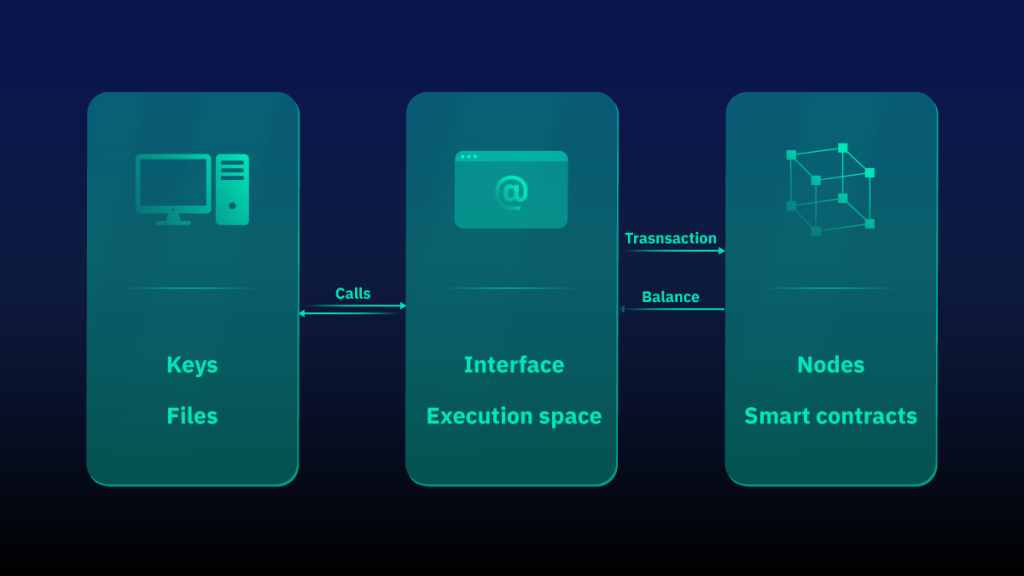
In fact, it is a combination of a web and a desktop wallet, since the application is installed and key files are stored on your device, but it is implemented as a browser extension. It is the best way to interact with decentralized applications. In addition, the use of such wallets does not require registration and allows you to remain anonymous. Access to an already installed extension with a generated address is obtained through the use of a password that serves as part of the encryption key for your private keys stored on the device.
+ Keys and assets are yours alone;
+ The most convenient type of wallet for interacting with dApps;
+ Completely anonymous;
– The loss of a seed phrase or a private key threatens a complete loss of assets;
– Inattentive connection to dubious protocols threatens a loss of assets;
– An internet connection is always required;
Examples: Metamask, Temple Wallet, Coinbase wallet
Conclusions
Different types of wallets are designed not only for different tasks but also for different audiences. Web wallets are the easiest way to work with assets because many of these wallets provide a way to restore access to your addresses and assets. Desktop wallets allow you to perform transactions without an internet connection and have increased security and advanced functionality. In turn, a wallet extension will be an indispensable tool for every user of decentralized applications. Choose your wallet’s type based on your qualifications, needs, and required blockchain using our examples as a guide.
Join our communities and follow us for more news and articles about blockchain, DeFi, and the Tezos ecosystem!
Telegram | Twitter | Discord | Reddit | Facebook

